Client-Side Vulnerabilities in Commercial Vpns
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Flexgw Ipsec VPN Image User Guide
FlexGW IPsec VPN Image User Guide Zhuyun Information Technology Co.,Ltd. www.cloudcare.cn Zhuyun Information Technology Co.,Ltd. Contents .......................................................................................................... .................................................................................................................. 1 Introduction 4 1.1 Software Compon.e..n..t.s................................................................................................................... 4 1.2 Login Description ................................................................................................................... 4 1.3 Function Description ....................................................................................................5 1.4 Typical Scenarios Des..c..r..i.p..t..i.o..n......................................................................................................5 1.5 Program Description .................................................................................6 1.6 Software Operation Command Summary ............................... 7 ............................................................................................................... 2 IPSec Site-to-Site VPN User Guide (VPC network scenario) 8 2.1 Start IPSec VPN.s..e..r..v..i.c..e.................................................................................................................8 2.2 Add new tunnel ................................................................................................................. -

Cisco VPN Client Administrator Guide Release 5.0 April 2010
Cisco VPN Client Administrator Guide Release 5.0 April 2010 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 Text Part Number: OL-5492-02 THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

Antmonitor: a System for Monitoring from Mobile Devices
AntMonitor: A System for Monitoring from Mobile Devices Anh Le Janus Varmarken Simon Langhoff CalIT2, UC Irvine IT Univ. of Copenhagen IT Univ. of Copenhagen [email protected] [email protected] [email protected] Anastasia Shuba Minas Gjoka Athina Markopoulou CalIT2, EECS, CPCC CalIT2, UC Irvine CalIT2, EECS, CPCC UC Irvine [email protected] UC Irvine [email protected] [email protected] ABSTRACT 1. INTRODUCTION We propose AntMonitor – a system for passive monitoring, Mobile devices, such as smart phones and tablets, have collection and analysis of fine-grained, large-scale packet become ubiquitous. With multiple wireless interfaces, in- measurements from Android devices. AntMonitor is the first cluding Wi-Fi and 3G/4G, these devices have persistent In- system of its kind that combines the following properties: (i) ternet connectivity throughout the day. In fact, the amount it provides participating users with fine-grained control of of traffic generated by these devices has grown rapidly in re- which data to contribute; (ii) it does not require administra- cent years and is expected to grow by 10 times in the next tive privileges; (iii) it supports client-side analysis of traffic; 5 years [1]. As a result, collecting and studying mobile net- and (iv) it supports collection of large-scale, fine-grained, work traffic has become a critical task in network infrastruc- and semantic-rich traffic. The first three properties benefit ture planning and Internet measurement research. mobile users, by giving them control over their privacy while There has been a rich body of literature that studies mo- also enabling a number of services to incentivize their par- bile network traffic [2, 3, 4, 5, 6]. -
![Arxiv:1907.07120V1 [Cs.CY] 16 Jul 2019 1 Introduction That China Hindered Access to I2P by Poisoning DNS Resolu- Tions of the I2P Homepage and Three Reseed Servers](https://docslib.b-cdn.net/cover/9451/arxiv-1907-07120v1-cs-cy-16-jul-2019-1-introduction-that-china-hindered-access-to-i2p-by-poisoning-dns-resolu-tions-of-the-i2p-homepage-and-three-reseed-servers-59451.webp)
Arxiv:1907.07120V1 [Cs.CY] 16 Jul 2019 1 Introduction That China Hindered Access to I2P by Poisoning DNS Resolu- Tions of the I2P Homepage and Three Reseed Servers
Measuring I2P Censorship at a Global Scale Nguyen Phong Hoang Sadie Doreen Michalis Polychronakis Stony Brook University The Invisible Internet Project Stony Brook University Abstract required flexibility for conducting fine-grained measurements on demand. We demonstrate these benefits by conducting an The prevalence of Internet censorship has prompted the in-depth investigation of the extent to which the I2P (invis- creation of several measurement platforms for monitoring ible Internet project) anonymity network is blocked across filtering activities. An important challenge faced by these different countries. platforms revolves around the trade-off between depth of mea- Due to the prevalence of Internet censorship and online surement and breadth of coverage. In this paper, we present surveillance in recent years [7, 34, 62], many pro-privacy and an opportunistic censorship measurement infrastructure built censorship circumvention tools, such as proxy servers, virtual on top of a network of distributed VPN servers run by vol- private networks (VPN), and anonymity networks have been unteers, which we used to measure the extent to which the developed. Among these tools, Tor [23] (based on onion rout- I2P anonymity network is blocked around the world. This ing [39,71]) and I2P [85] (based on garlic routing [24,25,33]) infrastructure provides us with not only numerous and ge- are widely used by privacy-conscious and censored users, as ographically diverse vantage points, but also the ability to they provide a higher level of privacy and anonymity [42]. conduct in-depth measurements across all levels of the net- In response, censors often hinder access to these services work stack. -

Implementation Single Account Pdc Vpn Based on Ldap
IMPLEMENTATION SINGLE ACCOUNT PDC VPN BASED ON LDAP Gregorius Hendita Artha Kusuma Teknik Informatika, Fakultas Teknik Universitas Pancasila [email protected] Abstrak Data is an important for the company. Centralized data storage to facilitate users for accessing data in the company. Data will be stored centrally with PDC (Primary Domain Controller). Build communicate between head office and branch office requires high cost for each connection is not enough to ensure safety and security of data. Exchange data between head office and branch office should be kept confidential. VPN (Virtual Private Network) makes communication more efficient, not only the cost affordable that connection, security and safety will be the primary facility of VPN (Virtual Private Network). Service were established in the system will be integrated using LDAP (Lightweight Directory Access Protocol) to create a single account in each services such as PDC (Primary Domain Controller) and VPN (Virtual Private Network). The purposes of this final project to design and implementation a system centralized data storage and build communicate between head office and branch office are integrated with LDAP (Lighweight Active Directory Protocol). Hopefully this system can give more advantage to each network users. Keyword: PDC, VPN, LDAP, Single Account. I. Introduction previous workstations. To support the performance of the employees of the company of course has a Centralized data storage makes it easy for users variety of network services are formed in it such as to access data. many companies need a ftp, mail server, file sharing etc. These services of centralized storage system, because the data is course have their respective accounts. -
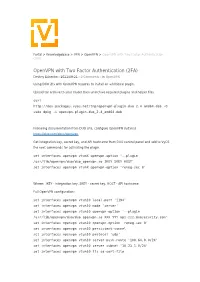
Openvpn with Two-Factor Authentication (2FA)
Portal > Knowledgebase > VPN > OpenVPN > OpenVPN with Two Factor Authentication (2FA) OpenVPN with Two Factor Authentication (2FA) Dmitriy Eshenko - 2021-09-21 - 0 Comments - in OpenVPN Using DUO 2fa with OpenVPN requires to install an additional plugin. Upload tar archive to your router then unarchive required plugins and helper files curl http://dev.packages.vyos.net/tmp/openvpn-plugin-duo_2.4_amd64.deb -O sudo dpkg -i openvpn-plugin-duo_2.4_amd64.deb Following documentation from DUO site, configure OpenVPN instance https://duo.com/docs/openvpn Get integration key, secret key, and API hostname from DUO control panel and add to VyOS the next commands for activating the plugin. set interfaces openvpn vtunX openvpn-option '--plugin /usr/lib/openvpn/duo/duo_openvpn.so IKEY SKEY HOST' set interfaces openvpn vtunX openvpn-option 'reneg-sec 0' Where: IKEY - integration key, SKEY - secret key, HOST - API hostname Full OpenVPN configuration: set interfaces openvpn vtun10 local-port '1194' set interfaces openvpn vtun10 mode 'server' set interfaces openvpn vtun10 openvpn-option '--plugin /usr/lib/openvpn/duo/duo_openvpn.so XXX YYY api-zzz.duosecurity.com' set interfaces openvpn vtun10 openvpn-option 'reneg-sec 0' set interfaces openvpn vtun10 persistent-tunnel set interfaces openvpn vtun10 protocol 'udp' set interfaces openvpn vtun10 server push-route '100.64.0.0/24' set interfaces openvpn vtun10 server subnet '10.23.1.0/24' set interfaces openvpn vtun10 tls ca-cert-file '/config/auth/ovpn/ca.crt' set interfaces openvpn vtun10 tls cert-file '/config/auth/ovpn/central.crt' set interfaces openvpn vtun10 tls crl-file '/config/auth/ovpn/crl.pem' set interfaces openvpn vtun10 tls dh-file '/config/auth/ovpn/dh.pem' set interfaces openvpn vtun10 tls key-file '/config/auth/ovpn/central.key' How to generate cryptographic materials described by the following link https://support.vyos.io/en/kb/articles/using-easy-rsa-to-generate-x-509-certificates-and-keys -2. -
Download Secure Vpn for Android Download Secure Vpn for Android
download secure vpn for android Download secure vpn for android. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Cloudflare Ray ID: 6686f3ad9d2384a4 • Your IP : 188.246.226.140 • Performance & security by Cloudflare. Download secure vpn for android. Password management for Android. Free account authenticator. Free Android private file storage. Free app for extra security. A powerful security tool for Android. Free VPN for mobile devices. Paid VPN service. Free VPN server access app. Free VPN for Android. Security app for mobile. Top Security & VPN. Add Us To Your Social Channels. Subscribe. Upgrade your lifestyle. Digital Trends helps readers keep tabs on the fast-paced world of tech with all the latest news, fun product reviews, insightful editorials, and one- of-a-kind sneak peeks. Digital Trends may earn a commission when you buy through links on our site. Download secure vpn for android. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. -

N2N: a Layer Two Peer-To-Peer VPN
N2N: A Layer Two Peer-to-Peer VPN Luca Deri1, Richard Andrews2 ntop.org, Pisa, Italy1 Symstream Technologies, Melbourne, Australia2 {deri, andrews}@ntop.org Abstract. The Internet was originally designed as a flat data network delivering a multitude of protocols and services between equal peers. Currently, after an explosive growth fostered by enormous and heterogeneous economic interests, it has become a constrained network severely enforcing client-server communication where addressing plans, packet routing, security policies and users’ reachability are almost entirely managed and limited by access providers. From the user’s perspective, the Internet is not an open transport system, but rather a telephony-like communication medium for content consumption. This paper describes the design and implementation of a new type of peer-to- peer virtual private network that can allow users to overcome some of these limitations. N2N users can create and manage their own secure and geographically distributed overlay network without the need for central administration, typical of most virtual private network systems. Keywords: Virtual private network, peer-to-peer, network overlay. 1. Motivation and Scope of Work Irony pervades many pages of history, and computing history is no exception. Once personal computing had won the market battle against mainframe-based computing, the commercial evolution of the Internet in the nineties stepped the computing world back to a substantially rigid client-server scheme. While it is true that the today’s Internet serves as a good transport system for supplying a plethora of data interchange services, virtually all of them are delivered by a client-server model, whether they are centralised or distributed, pay-per-use or virtually free [1]. -

Embedded Linux for Thin Clients Next Generation (Elux® NG) Version 1.25
Embedded Linux for Thin Clients Next Generation (eLux® NG) Version 1.25 Administrator’s Guide Build Nr.: 23 UniCon Software GmbH www.myelux.com eLux® NG Information in this document is subject to change without notice. Companies, names and data used in examples herein are fictitious unless otherwise noted. No part of this document may be reproduced or transmitted in any form or by any means, electronic or mechanical, for any purpose, without the express consent of UniCon Software GmbH. © by UniCon 2005 Software GmbH. All rights reserved eLux is a registered trademark of UniCon Software GmbH in Germany. Accelerated-X is a trademark of Xi Graphics, Inc. Adobe, Acrobat Reader and PostScript are registered trademarks of Adobe Systems Incorporated in the United States and/or other countries. Broadcom is a registered trademark of Broadcom Corporation in the U.S. and/or other countries. CardOS is a registered trademark and CONNECT2AIR is a trademark of Siemens AG in Germany and/or other countries. Cisco and Aironet are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and certain other countries. Citrix, Independent Computing Architecture (ICA), Program Neighborhood, MetaFrame, and MetaFrame XP are registered trademarks or trademarks of Citrix Systems, Inc. in the United States and other countries. CUPS and the Common UNIX Printing System are the trademark property of Easy Software Products. DivX is a trademark of Project Mayo. Ericom and PowerTerm are registered trademarks of Ericom Software in the United States and/or other countries. Gemplus is a registered trademark and GemSAFE a trademark of Gemplus. -

Webrtc IP Address Leaks Nasser Mohammed Al-Fannah Information Security Group Royal Holloway, University of London Email: [email protected]
1 One Leak Will Sink A Ship: WebRTC IP Address Leaks Nasser Mohammed Al-Fannah Information Security Group Royal Holloway, University of London Email: [email protected] Abstract—The introduction of the WebRTC API to modern browsers and mobile applications with Real-Time Commu- browsers has brought about a new threat to user privacy. nications (RTC) capabilities1. Apparently, identifying one or WebRTC is a set of communications protocols and APIs that provides browsers and mobile applications with Real-Time Com- more of the client IP addresses via a feature of WebRTC was 2 munications (RTC) capabilities over peer-to-peer connections. first reported and demonstrated by Roesler in 2015. In this The WebRTC API causes a range of client IP addresses to paper we refer to the WebRTC-based disclosure of a client IP become available to a visited website via JavaScript, even if a address to a visited website when using a VPN as a WebRTC VPN is in use. This is informally known as a WebRTC Leak, Leak. and is a potentially serious problem for users using VPN services The method due to Roesler can be used to reveal a for anonymity. The IP addresses that could leak include the client public IPv6 address and the private (or local) IP address. number of client IP addresses via JavaScript code executed The disclosure of such IP addresses, despite the use of a VPN on a WebRTC-supporting browser. Private (or internal) IP connection, could reveal the identity of the client as well as address(es) (i.e. addresses only valid in a local subnetwork) enable client tracking across websites. -

Express Vpn for Windows 10 Download How to Get an Expressvpn Free Trial Account – 2021 Hack
express vpn for windows 10 download How to Get an ExpressVPN Free Trial Account – 2021 Hack. The best way to make sure ExpressVPN is the right VPN for you is to take it for a test drive before you commit and make sure its features fit your needs. Unlike some other VPNs, ExpressVPN doesn’t have a standard free trial. But it does have a no-questions-asked, 30-day money-back guarantee. So you can test out the VPN with no limitations, risk-free. If at any point during those 30 days, you decide that ExpressVPN isn’t right for you, you can just request a refund. This is super simple: I’ve tested it using several accounts, and got my money back every time. ExpressVPN Free Trial : Quick Setup Guide. It’s easy to set up ExpressVPN and get your 30 days risk-free. Here’s a step-by-step walkthrough that will have you ready in minutes. Head over to the ExpressVPN free trial page, and select, “Start Your Trial Today” to go right to their pricing list. Choose your subscription plan length, and then enter your email address and payment details. Note that longer plans are much cheaper. ExpressVPN’s long-term plans are the most affordable. It’s easy to download the app to your device. The set up for the ExpressVPN app is simple, and fast. Request a refund via live chat. Try ExpressVPN risk-free for 30-days. Free Trial Vs. Money-Back Guarantee. The trial period for ExpressVPN is really a 30-day money-back guarantee, but this is better than a free trial. -

An Investigation Into the Security and Privacy of Ios VPN Applications
An Investigation Into the Security and Privacy of iOS VPN Applications Jack Wilson Division of Cybersecurity School of Design and Informatics Abertay University, Dundee A thesis submitted for the degree of Bachelor of Science with Honours in Ethical Hacking 1st May 2018 Word Count: 11,448 Abstract Due to the increasing number of recommendations for people to use VPN’s for privacy reasons, more app developers are creating VPN apps and publishing them on the Apple App Store and Google Play Store. In this ‘gold rush’, apps are being developed quickly and, in turn, not being developed with security fully in mind. This paper investigated a selection of free VPN applications available on the Apple App Store (for iOS devices) and test the apps for security and privacy. This includes testing for any traffic being transmitted over plain HTTP, DNS leakage and transmission of personally-identifiable information (such as phone number, IMEI 1, email address, MAC address) and evaluating the security of the tunnelling protocol used by the VPN. The testing methodology involved installing free VPN apps on a test device (an iPhone 6 running iOS 11), simulating network traffic for a pre-defined period of time and capturing the traffic (either through ARP spoofing, or through a proxy program such as Burpsuite). This allows for all traffic to be analysed to check for anything being sent without encryption. Other issues that often cause de-anonymisation with VPN applications such as DNS leakage can be tested using websites such as dnsleaktest.com. The research found several common security issues with the VPN applications that were tested, with a large majority of the applications tested failing to implement HTTPS.