Windows Xp Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Illustrated Tutorial: Creating a Bootable USB Flash Drive for Windows XP
Illustrated tutorial: Creating a bootable Version 1.0 February 15, 2007 USB flash drive for Windows XP By Greg Shultz The ability to boot Windows XP from a USB Flash Drive (UFD) offers endless possibilities. For example, you might make an easy-to-use troubleshooting tool for booting and analyzing seemingly dead PCs. Or you could transport your favorite applications back and forth from home to work without having to install them on both PCs. However, before you can create a bootable UFD, you must clear a few hurdles. You saw that one coming didn’t you? The first hurdle is having a PC in which the BIOS will allow you to configure the USB port to act as a bootable device. The second hurdle is having a UFD that that will work as a bootable device and that’s large enough and fast enough to boot an operating system such as Windows XP. The third hurdle is finding a way to condense and install Windows XP on a UFD. If you have a PC that was manufactured in the last several years, chances are that its BIOS will allow you to configure the USB port to act as a bootable device. If you have a good qual- ity UFD that’s at least 512 KB and that was manufactured in the last couple of years, you’ve probably cleared the second hurdle. And once you’ve cleared those first two hur- dles, the third one is a piece of cake. All you have to do is download and run some free soft- ware to create the bootable UFD. -

Windows XP History and Versions
Lecture 23: Windows XP History and Versions n Mid-80ies Microsoft and IBM cooperated to develop OS/2 n Windows XP is produced by Microsoft Co. n 1988 - Microsoft started to develop its own new technology (NT) OS n XP is multi-user, multi-process, preemptive multitasking OS, 30M lines of source code capable of running OS/2, Windows and Unix apps. Hired Dave Cutler - architect of DEC VAX/VMS to head the design n It is developed to support multiple platforms and targeted towards enterprise workstations and server market as well as n NT v. 3.1 first released commercially July 1993 desktops n NT v 4.0 adopted Windows 95 user interface, graphics code moved into kernel to improve performance n In today’s lecture n 2000 – improved networking and laptop support, support for plug-and- u XP’s predecessors, the history of XP design, XP versions play devices, support for more processors (up to 8) and memory, u design principles becomes true multi-user through terminal server u components n XP (released Oct 2001) – update for 2000 replacement for 95/98 F hardware abstraction layer u simplifies user interface, improved reliability, performance F executive improvements, partial 64-bit support F environmental subsystems n versions F file system u desktop: XP personal – 95/98 replacement, professional – advanced features like POSIX support, some network features 1 u server: .NET – support for web/print service, clusters, large memory2 and multiple processors Design goals Components n XP is microkernel-based, modular n security – NT was C-2 certified (US -

No More Excuses: Windows 7 Makes It Easy to Manage Computer Power
• Products that earn the ENERGY STAR® prevent greenhouse gas emissions by meeting strict energy efficiency guidelines set by the U.S. Environmental Protection Agency and the U.S. Department of Energy. www.energy star.gov NO MORE EXCUSES: WINDOWS 7 MAKES IT EASY TO MANAGE COMPUTER POWER CONSUMPTION ORGANIZATION-WIDE Here’s how you can take advantage of Windows 7’s new power management features The University of Wisconsin at Oshkosh is no stranger to the idea of sustainability. In 2003 it became the first university in the state to join the Environmental Protection Agency’s Green Power Partnership. Its green initiatives also earned the university high marks from the Sierra Club, which ranked the university nationally in its Cool Schools survey. Given this commitment to green, it’s no surprise that the university first deployed computer power management back in 2005, and that it was one of the first Energy Star power management success stories. At that time, the University’s computers ran the Windows XP and Windows 2000 operating systems, neither of which included native tools for the central administration of power management features. To implement power management settings on these machines, the University used third-party software from ENERGY STAR called EZ GPO. For detailed information and resources concerning Now that Windows 7 has CPM client management features built in, it’s much the power management of easier to administer power management. This case study will show you how the University of Wisconsin at Oshkosh took full advantage of computer power PCs running Windows XP, management features on Windows Vista and Windows 7 clients managed by please see the ENERGY STAR Windows Server 2008. -

Upgrading to Windows 7
Upgrading to Windows 7 Windows 7 was designed to upgrade from Windows Vista and not from Windows XP. Additionally, Microsoft will only allow the following upgrade path to Vista users: • Windows Vista Home Premium to Windows 7 Home Premium • Windows Vista Business to Windows 7 Professional • Windows Vista Enterprise to Windows 7 Enterprise • Windows Vista Ultimate to Windows 7 Ultimate ***Any other upgrade path from Vista to Windows 7 will require a clean install*** ***Any upgrade from Windows XP to Windows 7 will require a clean install*** Before proceeding with an installation of Windows 7, you are strongly advised to run Windows 7 Upgrade Advisor. Windows 7 Upgrade Advisor will check the compatibility of your computer with Windows 7 and alert you to any issues that you should address before installing Windows 7. The download is available at http://www.microsoft.com/windows/windows‐7/get/upgrade‐advisor.aspx. 1. From the Microsoft website click on Download the Windows Upgrade Advisor Beta. 2. Click Download and then click Run. 3. A window will display that says “Do you want to run this software?” Click Run. 4. On the Setup Wizard screen, click Next. 5. Click I accept the license terms and click Next. 6. Click Install. When installation is complete, click Close. 7. When you see the screen below, click Start Check. 8. Windows Upgrade Advisor will start checking compatibility. 9. Once the scan is complete, Upgrade Advisor will display any issues that you should be aware of. 10. Click Close to exit Windows Upgrade Advisor. You will be unable to do an in-place upgrade in the following situations: 1. -

Microsoft® Windows® XP Professional, Microsoft® Windows
Microsoft Windows XP Professional, Microsoft Windows XP Tablet PC Edition and Microsoft® Windows® XP Media Center Edition 2004 END-USER LICENSE AGREEMENT FOR MICROSOFT SOFTWARE IMPORTANT—READ CAREFULLY: This End-User License Agreement (“EULA”) is a legal agreement between you (either an individual or a single entity) and the manufacturer ("Manufacturer") of the computer system or computer system component (“HARDWARE”) with which you acquired the Microsoft software product(s) identified on the Certificate of Authenticity ("COA") affixed to the HARDWARE or on the associated product documentation (“SOFTWARE”). The SOFTWARE includes Microsoft computer software, and may include associated media, printed materials, “online” or electronic documentation, and Internet based services. Note, however, that any software, documentation, or web services that are included in the SOFTWARE, or accessible via the SOFTWARE, and are accompanied by their own license agreements or terms of use are governed by such agreements rather than this EULA. The terms of a printed paper EULA, which may accompany the SOFTWARE, supersede the terms of any on-screen EULA. This EULA is valid and grants the end-user rights ONLY if the SOFTWARE is genuine and a genuine Certificate of Authenticity for the SOFTWARE is included. For more information on identifying whether your software is genuine, please see http://www.microsoft.com/piracy/howtotell. YOU AGREE TO BE BOUND BY THE TERMS OF THIS EULA BY INSTALLING, COPYING, OR OTHERWISE USING THE SOFTWARE. IF YOU DO NOT AGREE TO THE TERMS OF THIS EULA, YOU MAY NOT USE OR COPY THE SOFTWARE, AND YOU SHOULD PROMPTLY CONTACT MANUFACTURER FOR INSTRUCTIONS ON RETURN OF THE UNUSED PRODUCT(S) FOR A REFUND IN ACCORDANCE WITH MANUFACTURER’S RETURN POLICIES. -
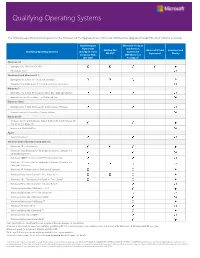
Qualifying Operating Systems
Qualifying Operating Systems The following operating systems qualify for the Windows 10 Pro Upgrade and/or Windows 10 Enterprise Upgrade through Microsoft Volume Licensing. New Enterprise Microsoft Products Agreement and Services Existing EA/ Microsoft Cloud Academic and Qualifying Operating Systems (EA)/Open Value Agreement OV-CW2 Agreement Charity Company-Wide (MPSA)/Select (OV-CW)1 Plus/Open3 Windows 10 4 Enterprise (N, KN) , Pro (N, KN) Education, Home Windows 8 and Windows 8.1 Enterprise (N, K, KN), Pro (N, K, KN, diskless) Windows 8 and Windows 8.1 (including Single Language) Windows 7 Enterprise (N, K, KN), Professional (N, K, KN, diskless), Ultimate Home Premium, Home Basic, or Starter Edition Windows Vista Enterprise (N, K, KN), Business (N, K, KN, Blade), Ultimate Home Premium, Home Basic, Starter Edition Windows XP Professional (N, K, KN, Blade), Tablet Edition (N, K, KN, Blade), XP Pro N, XP Pro Blade PC Home and Starter Edition Apple Apple Macintosh Windows Embedded Operating Systems Windows 10 IoT Enterprise Windows Vista Business for Embedded Systems, Ultimate for Embedded Systems Windows 2000 Professional for Embedded Systems Windows 7 Professional for Embedded Systems, Ultimate for Embedded Systems Windows XP Professional for Embedded Systems Windows Embedded 8 and 8.1 Pro, Industry Pro Windows 10 IoT Enterprise for Retail or Thin Clients5 5 Windows Embedded 8 and 8.1 Industry Retail Windows Embedded POSReady 7 Pro5 5 Windows Embedded for Point of Service Windows Embedded POSReady 20095 5 Windows Embedded POSReady 7 5 Windows XP Embedded Windows Embedded Standard 75 5 Windows Embedded 2009 5 Windows Embedded 8 Standard 1Also applicable to Qualified Devices acquired through merger or acquisition. -

Windows XP's End of Life
Windows XP’s End of Life Understanding the Risks and Impact to Point-of-Sale and Automated Teller Machines Introduction An era is passing. The reconfirmed they will continue venerable workhorse of to update the anti-malware personal computer operating engine and signatures through systems Windows XP was 14 July 2015. removed from Microsoft’s Introduced in 2001, XP was the list of supported operating most widely used operating systems on 8 April 2014. system up until August 2012, Announced in 2007, this end when it was surpassed by of support means Microsoft Windows 7. As of February will no longer release any XP 2014, Windows XP still resides software updates, automatic on roughly 30% of personal fixes or service packs. Support computers worldwide. for Windows XP Embedded systems expires on 12 January 1 Microsoft Embedded Product Lifecycles & Support 2016.1 However, Microsoft © 2014 Visa. All Rights Reserved. Today, many Point-of-Sale (POS) payment applications were programmed to reside on personal computers running XP. Windows XP is already a highly vulnerable platform based on its longevity OVER and its overall architecture. Modern operating systems like Windows 7 and 8 have more sophisticated security features built in, making them less of a target to hackers, who would rather exploit vulnerabilities in older unpatched systems versus expending time and energy developing exploits only to have them undone by a monthly security patch. Anyone using Windows XP, 95% whether it is for personal computing or business operations, should be planning now to upgrade to of the world’s ATMs are a newer and more secure operating system. -

Upgrading from Windows XP to Windows 7
Upgrading from Windows XP to Windows 7 Overview In this Tutorial Note: We highly recommend printing out this Step 1: Run Windows 7 Upgrade Advisor 2 tutorial. The Windows 7 installation process will Step 2: Move files and settings 3 restart your computer. If you don't return to this Step 3: Install Windows 7 5 webpage, the printed instructions will help you Step 4: Restore files and settings 8 complete the installation process. Introduction Windows XP can't use the Upgrade installation What You’ll Need option to install Windows 7. However, you can still An external hard drive or large capacity USB install Windows 7 by selecting the Custom option flash drive instead. An Internet connection This tutorial guides you through the process of A Windows 7 installation disc using Windows Easy Transfer to move your files and settings off of your PC, installing Windows 7 using the Custom option, and then moving your files back to your PC. Be sure to read the tutorial thoroughly before following the steps. Before you begin A Custom installation has several important differences from the Upgrade option that you need to know about: A Custom installation of Windows does not preserve your programs, files, or settings. It’s sometimes called a “clean” install for that reason. You’ll need to reinstall your programs. This means that you'll also need the original program installation discs or setup files for any programs that you want to install in Windows 7. You'll need to save your files to an external location off of your PC before you install Windows 7. -

Win Xp Pe Iso Download
Win Xp Pe Iso Download 1 / 4 Win Xp Pe Iso Download 2 / 4 3 / 4 Download Files. Download PEbuilder 3.1.10 File: Download PEbuilder 3.1.10 File. BartPE Iso WINXP Emulated Version 155MB: .... To start working with WinPE, download and install both the Windows ... To learn how to create a bootable WinPE CD, DVD, ISO, or VHD, see .... A tutorial on installing BartPE onto a bootable USB drive. ... but instead of going straight into the BartPE OS, it loaded the BartPE ISO file into the ... Secondly, download Microsoft's Windows Server 2003 SP1 installation file (this can ... This utility has the ability to properly format a USB disk & install a Windows XP boot sector.. Jump to Boot WinPE/BartPE from an ISO file - Download firadisk.gz from the Beta ... For example, for the Avast BartPE ISO you can use a .... Download BartPE builder from http://www.nu2.nu/pebuilder/ ... When it's done building, image file "c:\pebuilder\pebuilder.iso" should be created properly.. Use Windows 7/XP ISO File or DVD to Create Bootable Install USB Drive ... it also allows you transfer Windows PE( Windows XP / Windows 7 / Vista / 2003 / 2008 ) to usb pen drive in a few clicks. ... Download it from softpedia.. Here we show you 5 Windows PE based boot discs to help technicians and ... disc is fully automated including the downloading of the Windows ISO image file.. 1.1 USB Drive; 1.2 BIOS/UEFI configuration; 1.3 ISO image ... If not, download BartPE; The original CD of Windows XP Professional, not a Windows XP Home ... -
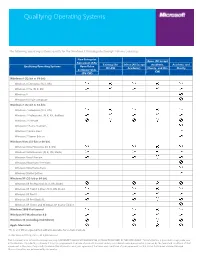
Qualifying Operating Systems
Qualifying Operating Systems The following operating systems qualify for the Windows 8 Pro Upgrade through Volume Licensing. New Enterprise Open (All Except Agreement (EA)/ Existing EA/ Select (All Except Academic, Academic and Qualifying Operating Systems Open Value OV-CW Academic) Charity, and OV- Charity Company-wide CW) (OV-CW) Windows 8 (32-bit or 64-bit) Windows 8 Enterprise (N, K, KN) Windows 8 Pro (N, K, KN) Windows 8 Windows 8 Single Language Windows 7 (32-bit or 64-bit) Windows 7 Enterprise (N, K, KN) Windows 7 Professional (N, K, KN, diskless) Windows 7 Ultimate Windows 7 Home Premium Windows 7 Home Basic Windows 7 Starter Edition Windows Vista (32-bit or 64-bit) Windows Vista Enterprise (N, K, KN) Windows Vista Business (N, K, KN, Blade) Windows Vista Ultimate Windows Vista Home Premium Windows Vista Home Basic Windows Starter Edition Windows XP (32-bit or 64-bit) Windows XP Professional (N, K, KN, Blade) Windows XP Tablet Edition (N, K, KN, Blade) Windows XP Pro N Windows XP Pro Blade PC Windows XP Home and Windows XP Starter Edition Windows 2000 Professional Windows NT Workstation 4.0 Windows 98 (including 2nd Edition) Apple Macintosh *N, K, and KN are specialized editions available for certain markets. © 2012 Microsoft Corporation. All rights reserved. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS DOCUMENT. This information is provided to help guide your authorized use of products you license; it is not your agreement. Your use of products licensed under your volume license agreement is governed by the terms and conditions of that agreement. -

Installing and Using Windows XP Professional ‐ Chapter #15
Installing and Using Windows XP Professional ‐ Chapter #15 Amy Hissom Key Terms Automated System Recovery (ASR) - The Windows XP process that allows you to restore an entire hard drive volume or logical drive to its state at the time the backup of the volume was made. Boot loader menu — A startup menu that gives the user the choice of which operating system to load such as Windows 98 or Windows XP which are both installed on the same system, creating a dual boot. Compatibility Mode utility — A Windows XP utility that provides an application with the older Microsoft OS environment it was designed to operate in. Product activation — The process that Microsoft uses to prevent software piracy. For example, once Windows XP is activated for a particular computer, it cannot be installed on another computer. Remote Assistance — A Windows XP feature that allows a support technician at a remote location to have full access to the Windows XP desktop. User State Migration Tool (USMT) — A Windows XP utility that helps you migrate user files and preferences from one computer to another in order to help a user makes a smooth transition from one computer to another. Review Questions Name the 5 versions of Windows XP. XP 64-bit Edition, XP Home Edition, XP Professional, XP Media Center Edition, and XP Tablet PC Edition 1.) What are at least 3 similarities between Windows XP and Windows 2000? At least 3 differences? Windows XP uses the same kernel architecture as Windows 2000. The desktop is very different looking. There is more added support for multimedia and networking technologies in Windows XP. -

GENESIS32 – DCOM on Windows XP and Server 2003 in a Domain December 2007 Description: Guide to Setup DCOM on a Windows XP Or 4
GENESIS32 – DCOM on Windows XP and Server 2003 in a Domain December 2007 Description: Guide to setup DCOM on a Windows XP or 4. The My Computer Properties window will open. Click on Windows Server 2003 Operating System when computers are in the Default Properties tab, and match the properties as a domain on the Local Area Network. shown in Figure 2. OS Requirement: Windows XP/Server 2003. General Requirement: In order to communicate OPC data between different PCs via DCOM in a domain, the following requirements apply: • All GENESIS32 machines must be in the same domain on the LAN. • All GENESIS32 machines must be logged in to the operating system with a domain user. • The password must not be blank or “admin”. • The user must have administrative privileges to the local PC to change the DCOM settings. • Windows XP machines must have SP1 installed. Introduction For GENESIS32 Applications to communicate via DCOM, it is necessary to allow Access and Launch permissions for specific users. This application note explains how to setup DCOM on a Windows XP or Windows Server 2003 Operating System, for the most wide-open permissions. It is usually helpful to develop your application with wide-open communications to be sure that it all works properly. After you have completed your Figure 2 - My Computer Default Properties development, you will want to tighten these permissions until you reach a desired level of security 5. Next we have to add user permissions to the Default Security. Click the Default COM Security tab as shown in Editing DCOM Settings Figure 3 1.