List of Application Added in ARL #2613
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Vectorcast Installation Guide for Vectorcast 2021
New editions of this guide incorporate all material added or changed since the previous edition. Update packages may be used between editions. The manual printing date changes when a new edition is printed. The contents and format of this manual are subject to change without notice. Generated: 7/25/2021, 8:48 PM Rev: 33d0493 Part Number: VectorCAST Installation Guide for VectorCAST 2021 VectorCAST is a trademark of Vector Informatik, GmbH © Copyright 2021, Vector Informatik, GmbH All rights reserved. No part of the material protected by this copyright notice may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying, recording, or by any informational storage and retrieval system, without written permission from the copyright owner. U.S. Government Restricted Rights This computer software and related documentation are provided with Restricted Rights. Use, duplication or disclosure by the Government is subject to restrictions as set forth in the governing Rights in Technical Data and Computer Software clause of DFARS 252.227-7015 (June 1995) and DFARS 227.7202-3(b). Manufacturer is Vector North America, Inc. East Greenwich RI 02818, USA. Vector Informatik reserves the right to make changes in specifications and other information contained in this document without prior notice. Contact Vector Informatik to determine whether such changes have been made. Third-Party copyright notices are contained in the file: 3rdPartyLicenses.txt, located in the VectorCAST installation directory. 2 TABLE OF -

Flexnet Server
FlexNet Server Administration Guide Copyright Copyright © 2019 CAXperts GmbH. All Rights Reserved. Including software, file formats, and audio-visual displays; may be used pursuant to applicable software licence agreement; contains confidential and proprietary information of CAXperts and/or third parties which is protected by copyright law, trade secret law, and international treaty, and may not be provided or otherwise made available without proper authorisation. Restricted Rights Legend Rights reserved under the copyright laws of the Federal Republic of Germany. Warranties and Liabilities All warranties given by CAXperts about equipment or software are set forth in your purchase contract, and nothing stated in, or implied by, this document or its contents shall be considered or deemed a modification or amendment of such warranties. CAXperts believes the information in this publication is accurate as of its publication date. The information and the software discussed in this document are subject to change without notice and are subject to applicable technical product descriptions. CAXperts is not responsible for any error that may appear in this document. The software discussed in this document is furnished under a licence and may be used or copied only in accordance with the terms of this licence. THE USER OF THE SOFTWARE IS EXPECTED TO MAKE THE FINAL EVALUATION AS TO THE USEFULNESS OF THE SOFTWARE IN HIS OWN ENVIRONMENT. Trademarks CAXperts is a registered trademark of CAXperts GmbH. Intergraph, the Intergraph logo, SmartSketch, FrameWorks, SmartPlant, INtools, MARIAN, PDS, IGDS, RIS and IntelliShip are registered trademarks of Intergraph Corporation. IGDS file formats ©1987-1994 Intergraph Corporation. Microsoft and Windows are registered trademarks of Microsoft Corporation. -

False Alarm Test February 2011
Anti-Virus Comparative - Appendix – February 2011 www.av-comparatives.org Details about Discovered False Alarms Appendix to the Anti-Virus Comparative February 2011 Language: English February 2011 Last Revision: 29th March 2011 www.av-comparatives.org - 1 - Anti-Virus Comparative - Appendix – February 2011 www.av-comparatives.org Details about the discovered false alarms With AV testing it is important to measure not only detection capabilities but also reliability - one of reliability aspects is certainly product's tendency to flag clean files as infected. No product is immune from false positives (FP’s) but there are differences among them and the goal is to measure them. Nobody has all legitimate files that exist and so no "ultimate" test of FP’s can be done. What can be done and is reasonable, is to create and use a set of clean files which is independent. If on such set one product has e.g. 50 FP’s and another only 10, it is likely that the first product is more prone to FP’s than the other. It doesn't mean the product with 10 FP’s doesn't have more than 10 FP’s globally, but important is the relative number. All listed false alarms were reported and sent to the Anti-Virus vendors for verification and should now be already fixed. False alarms caused by unencrypted data blocks in Anti-Virus related files were not counted. If a product had several false alarms belonging to the same software, it is counted here as only one false alarm. Cracks, keygens, etc. -
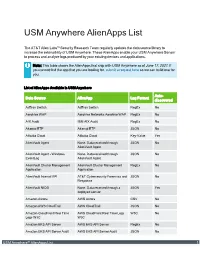
USM Anywhere Alienapps List
USM Anywhere AlienApps List The AT&T Alien Labs™ Security Research Team regularly updates the data source library to increase the extensibility of USM Anywhere. These AlienApps enable your USM Anywhere Sensor to process and analyze logs produced by your existing devices and applications. Note: This table shows the AlienApps that ship with USM Anywhere as of June 17, 2021. If you cannot find the app that you are looking for, submit a request here so we can build one for you. List of AlienApps Available in USM Anywhere Auto- Data Source AlienApp Log Format discovered AdTran Switch AdTran Switch RegEx No Aerohive WAP Aerohive Networks Aerohive WAP RegEx No AIX Audit IBM AIX Audit RegEx No Akamai ETP Akamai ETP JSON No Alibaba Cloud Alibaba Cloud Key-Value Yes AlienVault Agent None. Data received through JSON No AlienVault Agent AlienVault Agent - Windows None. Data received through JSON No EventLog AlienVault Agent AlienVault Cluster Management AlienVault Cluster Management RegEx No Application Application AlienVault Internal API AT&T Cybersecurity Forensics and JSON No Response AlienVault NIDS None. Data received through a JSON Yes deployed sensor Amazon Aurora AWS Aurora CSV No Amazon AWS CloudTrail AWS CloudTrail JSON No Amazon CloudFront Real Time AWS CloudFront Real Time Logs W3C No Logs W3C W3C Amazon EKS API Server AWS EKS API Server RegEx No Amazon EKS API Server Audit AWS EKS API Server Audit JSON No USM Anywhere™ AlienApps List 1 List of AlienApps Available in USM Anywhere (Continued) Auto- Data Source AlienApp Log Format discovered -

Flexnet Publisher Release Notes
FlexNet Publisher 2018 R4 (11.16.2) Release Notes December 2018 Revision 00 Enhancements ................................................................................................................................. 3 Security Updates.............................................................................................................................. 3 Dongle Updates ............................................................................................................................... 4 Platform Updates............................................................................................................................. 4 11.16.2 Updates ............................................................................................................................................4 Windows........................................................................................................................................................................................................ 4 macOS/OS X ................................................................................................................................................................................................ 4 Integrated Products and Tested Versions........................................................................................................................................ 4 11.16.1 Updates ............................................................................................................................................4 -

Ovum Market Radar: Password Management Tools
Ovum Market Radar: Password Management Tools Improving cybersecurity by eliminating weak, reused, and compromised passwords Publication Date: 17 Aug 2019 | Product code: INT005-000010KEEPER Richard Edwards Ovum Market Radar: Password Management Tools Summary Catalyst Cybersecurity often depends on the choices made by individuals. Most of these individuals are conscientious when it comes to preserving the confidentiality, integrity, and availability of corporate systems and customer data. However, if we consider the ways in which passwords and account credentials are used and managed, we can easily see weaknesses in our cybersecurity defenses. Password management tools have entered the mainstream, with more than 70 apps competing for user attention in the Google Play Store alone. There’s also a good selection of products targeting teams, businesses, and enterprises. However, these products need to adapt and evolve to win new business, protect against new cybersecurity threats, and support the move toward a “password-less” enterprise. Ovum view Key findings from an Ovum survey of IT decision-makers and enterprise employees reveals that password management practices are out of date, overly reliant on manual processes, and highly dependent on employees “doing the right thing”. If the alarm bell isn’t ringing, it should be. Cybersecurity training and awareness programs are useful, but to keep the business safe and secure, employees across all roles and at all levels require tools and applications to help alleviate the burden and risks associated with workplace passwords, credentials, logins, and access codes. Key messages ▪ Passwords are for more than just the web. Credentials and passcodes are required for desktop applications, mobile apps, IT infrastructure, physical access, and more. -

License Administration Guide Flexnet Publisher Licensing Toolkit 11.10.1 Legal Information
License Administration Guide FlexNet Publisher Licensing Toolkit 11.10.1 Legal Information Book Name: License Administration Guide Part Number: FNP-11101-LAG00 Product Release Date: February 2012 Copyright Notice Copyright © 2012 Flexera Software LLC. All Rights Reserved. This product contains proprietary and confidential technology, information and creative works owned by Flexera Software LLC and its licensors, if any. Any use, copying, publication, distribution, display, modification, or transmission of such technology in whole or in part in any form or by any means without the prior express written permission of Flexera Software LLC is strictly prohibited. Except where expressly provided by Flexera Software LLC in writing, possession of this technology shall not be construed to confer any license or rights under any Flexera Software LLC intellectual property rights, whether by estoppel, implication, or otherwise. All copies of the technology and related information, if allowed by Flexera Software LLC, must display this notice of copyright and ownership in full. FlexNet Publisher incorporates software developed by others and redistributed according to license agreements. Copyright notices and licenses for these external libraries are provided in a supplementary document that accompanies this one. Trademarks Flexera Software, AdminStudio, FlexEnabled, FlexLM, FlexNet, FlexNet Connect, FlexNet Manager, FlexNet Publisher, InstallAnywhere, InstallShield, InstallShield Professional, and PackageExpert are registered trademarks or trademarks -

License Activation Center Administration Quick Start
License Activation Center Administration Quick Start This Quick Start for License Activation Center (LAC) administrators takes you through a simple example to quickly learn how to: 1. Log into the administrative area of LAC. 2. Add a license generator. 3. Add a product and product features. 4. Create templates for the product. 5. Add customers. 6. Create license orders using product templates. 7. Activate a license. Logging into LAC First, log into the administrative area of LAC by going to https://license.x-formation.com. From this page, log in by entering your username and password in the login box. If the login box is asking for an activation key, you are on the end-user login page. Click the Log in as a license administrator link at the bottom of the login box to switch to the administrator login. Note: LAC does not support concurrent logins using the same user credentials. If a user logs into LAC using the same username and password as another user that is currently logged into LAC, the currently logged in user will be signed out of LAC automatically. (Users are also automatically signed out after 1 hour of idleness when using the UI or 3 hours of idleness using SOAP.) Adding a license generator You must define a license generator for each product you'll add to LAC. It's easiest to add the license generator before adding the product that will use it. Since you can use the license generator you add during this quickstart for your own LAC products, enter values that will define a real license generator for your environment. -

Veracryptcrypt F R E E O P E N - S O U R C E O N - T H E - F L Y E N C R Y P T I O N User’S Guide
VERAVERACRYPTCRYPT F R E E O P E N - S O U R C E O N - T H E - F L Y E N C R Y P T I O N USER’S GUIDE veracrypt.codeplex.com Version Information VeraCrypt User’s Guide, version 1.19 Released by IDRIX on October 17th, 2016 Legal Notices THIS DOCUMENT IS PROVIDED "AS IS" WITHOUT WARRANTY OF ANY KIND, WHETHER EXPRESS, IMPLIED, OR STATUTORY. THE ENTIRE RISK AS TO THE QUALITY, CORRECTNESS, ACCURACY, OR COMPLETENESS OF THE CONTENT OF THIS DOCUMENT IS WITH YOU. THE CONTENT OF THIS DOCUMENT MAY BE INACCURATE, INCORRECT, INVALID, INCOMPLETE AND/OR MISLEADING. IN NO EVENT WILL ANY AUTHOR OF THE SOFTWARE OR DOCUMENTATION, OR ANY APPLICABLE COPYRIGHT OWNER, OR ANY OTHER PARTY WHO MAY COPY AND/OR (RE)DISTRIBUTE THIS SOFTWARE OR DOCUMENTATION, BE LIABLE TO YOU OR TO ANY OTHER PARTY FOR ANY DAMAGES, INCLUDING, BUT NOT LIMITED TO, ANY DIRECT, INDIRECT, GENERAL, SPECIAL, INCIDENTAL, PUNITIVE, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, CORRUPTION OR LOSS OF DATA, ANY LOSSES SUSTAINED BY YOU OR THIRD PARTIES, A FAILURE OF THIS SOFTWARE TO OPERATE WITH ANY OTHER PRODUCT, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES, OR BUSINESS INTERRUPTION), WHETHER IN CONTRACT, STRICT LIABILITY, TORT (INCLUDING, BUT NOT LIMITED TO, NEGLIGENCE) OR OTHERWISE, ARISING OUT OF THE USE, COPYING, MODIFICATION, OR (RE)DISTRIBUTION OF THIS SOFTWARE OR DOCUMENTATION (OR A PORTION THEREOF), OR INABILITY TO USE THIS SOFTWARE OR DOCUMENTATION, EVEN IF SUCH DAMAGES (OR THE POSSIBILITY OF SUCH DAMAGES) ARE/WERE PREDICTABLE OR KNOWN TO ANY (CO)AUTHOR, INTELLECTUAL-PROPERTY OWNER, OR ANY OTHER PARTY. -

Flexnet Publisher Monetize and Protect Your IP with Flexible Software Licensing—On-Premises
FlexNet Publisher Monetize and Protect Your IP with Flexible Software Licensing—On-Premises, DATASHEET SaaS, Cloud and Virtualized The software industry continues to change. Slow on-premises, SaaS, Cloud or virtualized application. “IT buyers wish to focus revenue growth, mergers and acquisitions, piracy, It enables you to monetize and protect your IP to on allocating resources virtualization, SaaS, the Cloud, and the growing realize increased revenues and experience greater more efficiently and demand for utility-based software licensing models market penetration. generating ROI, which are just a few of the forces reshaping the landscape. means negotiating the most beneficial license Cut Support Costs with Easy End-User License agreements. In this To cope with these changes, software vendors and Management environment, FlexNet intelligent device manufacturers must find ways With other licensing solutions, when customers Publisher can help to boost sales by offering customers the licensing install or move licenses, errors often occur that software vendors deliver options they want, while preventing revenue loss by frustrate end users and increase your support costs. customized licensing protecting software IP from unlicensed use. FlexNet Publisher lets you offer customers a way solutions and the terms to activate and change licenses while maintaining to go with them.” Grow Revenue with Flexible Software Licensing, compliance. With FlexNet Publisher, activations and license changes are reduced to a single click, so – Amy Konary Pricing, and Packaging Research Director FlexNet Publisher gives you flexibility to customize customers can start using your products more quickly Software Pricing, software pricing, packaging, and licensing terms for without involving your support staff. -

LAM Guide Linux, Solaris, and Windows
LAM Guide Linux, Solaris, and Windows © 2008 Landmark Graphics Corporation Part No. 161608 R5000.0.0 February 2008 © 2008 Landmark Graphics Corporation All Rights Reserved Worldwide This publication has been provided pursuant to an agreement containing restrictions on its use. The publication is also protected by Federal copyright law. No part of this publication may be copied or distributed, transmitted, transcribed, stored in a retrieval system, or translated into any human or computer language, in any form or by any means, electronic, magnetic, manual, or otherwise, or disclosed to third parties without the express written permission of: Landmark Graphics Corporation 2107 CityWest Blvd, Building 2, Houston, Texas 77042-3021, USA P.O. Box 42806, Houston, Texas 77242, USA Phone: 713-839-2000 FAX: 713-839-2401 Web: www.halliburton.com/landmark Trademark Notice 3D Drill View, 3D Drill View KM, 3DFS, 3D Surveillance, 3DView, Active Field Surveillance, Active Reservoir Surveillance, ADC, Advanced Data Transfer, ARIES, ARIES DecisionSuite, Asset Decision Solution, Asset Development Center, Asset Journal, AssetLink, AssetLink Advisor, AssetLink Director, AssetLink Observer, Asset Performance, AssetPlanner, AssetSolver, AssetSolver Online, AssetView, BLITZPAK, CasingSeat, COMPASS, Corporate Data Archiver, Corporate Data Store, Data Analyzer, DataManager, DataStar, DBPlot, DecisionSpace, DecisionsSpace 3D Drill View KM, DecisionSpace AssetLink, DecisionSpace AssetPlanner, DecisionSpace AssetSolver, DecisionSpace AssetView 2D, DecisionSpace AssetView -

Die Verschiedenen Editionen Im Vergleich
Die verschiedenen Versionen im Vergleich Community Enterprise Funktion Enterprise+ Edition Edition Sensible Daten teilen Teilen Sie sensible Daten wie Passwörter und schützenswerte Informationen. Nutzer verwalten Sie haben die Möglichkeit, einzelne Nutzer manuell zu erstellen, zu löschen, zu bearbeiten oder zu sperren, ihnen Rollen zuzuweisen oder Passwörter zu ändern etc. Rollen verwalten Definieren Sie Nutzerrollen, erteilen Sie spezifische Berechtigungen und/oder wählen Sie Unterrollen aus. KeePass-Schnittstelle für Pleasant Password Server Laden Sie KeePass mittels der sicheren und nutzerfreundlichen KeePass Manager- Schnittstelle herunter. Webbasieter Zugriff Geben Sie die Zugangsdaten mühelos mithilfe des Web-Clients ein. Ordnerverwaltung Fügen Sie Ordner oder Einträge hinzu, und bearbeiten, verschieben oder löschen Sie Ordner. Community Enterprise Funktion Enterprise+ Edition Edition Private Ordner Erstellen Sie mit nur einem Klick besonders geschützte Ordner (diese können sichtbar oder unsichtbar sein). Dateianhänge schützen Schützen Sie Dateien auf dieselbe Weise wie Ihre Passwörter. Sicherheitsansicht Sehen Sie, welche Zugangsmöglichkeiten den verschiedenen Nutzern und Rollen in Bezug auf den jeweiligen Ordner zustehen. Kundenspezifische Web Client-Einstellungen Nutzen Sie verschiedene Optionen, wie beispielswiese das „Hide Client Download Tab“, wenn es sich nur um den Web Client handelt. Ordnersymbole anpassen Passen Sie Eingangs- und Gruppensymbole individuell an Ihre persönlichen Designvorstellung an. Umfassende Berichte