Machine Learning and Understanding for Intelligent Extreme Scale Scientific Computing and Discovery
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Springer Top Titles in Natural Sciences & Engineering
ABC springer.com Springer Top Titles in Natural Sciences & Engineering New Book Information FIRST QUARTER 2013 ABC springer.com Available The Reorientation of Higher Education ISBN 978-94-007-5847-6 Challenging the East-West Dichotomy 2013. IX, 314 p. 5 illus. (CERC Studies B. Adamson, Hong Kong Institute of Education, China; J. Nixon, University of Sheffield, UK; in Comparative Education, Volume 31) F. Su, Liverpool Hope University, UK (Eds) Hardcover Features 7 € 129,95 | £117.00 7 Focusses on the nature of, and conditions necessary for, the transformation 7 * € (D) 139,05 | € (A) 142,94 | sFr 173,00 of higher education Bookstore Location 7 Exemplifies the complexities of the process of institutional change across Education regional, national and continental divides 7 Challenges the notion of an East-West dichotomy in institutional Fields of interest repositionings International and Comparative Education; Higher Education; Educational Policy and This book presents accounts of the repositioning of higher education institutions across a range Politics of contexts in the East and the West. It argues that global governance, institutional organisation and academic practice are complementary elements within the process of institutional Target groups repositioning. While systems, institutions and individuals in the different contexts are subjected Research to similar global trends and pressures, the reorientation of higher education takes diverse forms Product category as a result of the particularities of those contexts. That reorientation cannot be explained in terms of East-West dichotomies and divisions, but only with reference to the interflow across and Contributed volume within systems. Globalisation necessitates complex interconnectivities of regionality, culture and geopolitics that this book explores in relation to specific cases and contexts. -
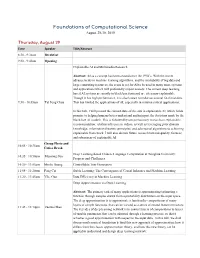
Foundations of Computational Science August 29-30, 2019
Foundations of Computational Science August 29-30, 2019 Thursday, August 29 Time Speaker Title/Abstract 8:30 - 9:30am Breakfast 9:30 - 9:40am Opening Explainable AI and Multimedia Research Abstract: AI as a concept has been around since the 1950’s. With the recent advancements in machine learning algorithms, and the availability of big data and large computing resources, the scene is set for AI to be used in many more systems and applications which will profoundly impact society. The current deep learning based AI systems are mostly in black box form and are often non-explainable. Though it has high performance, it is also known to make occasional fatal mistakes. 9:30 - 10:05am Tat Seng Chua This has limited the applications of AI, especially in mission critical applications. In this talk, I will present the current state-of-the arts in explainable AI, which holds promise to helping humans better understand and interpret the decisions made by the black-box AI models. This is followed by our preliminary research on explainable recommendation, relation inference in videos, as well as leveraging prior domain knowledge, information theoretic principles, and adversarial algorithms to achieving explainable framework. I will also discuss future research towards quality, fairness and robustness of explainable AI. Group Photo and 10:05 - 10:35am Coffee Break Deep Learning-based Chinese Language Computation at Tsinghua University: 10:35 - 10:50am Maosong Sun Progress and Challenges 10:50 - 11:05am Minlie Huang Controllable Text Generation 11:05 - 11:20am Peng Cui Stable Learning: The Convergence of Causal Inference and Machine Learning 11:20 - 11:45am Yike Guo Data Efficiency in Machine Learning Deep Approximation via Deep Learning Abstract: The primary task of many applications is approximating/estimating a function through samples drawn from a probability distribution on the input space. -

Kitsune: an Ensemble of Autoencoders for Online Network Intrusion Detection
Kitsune: An Ensemble of Autoencoders for Online Network Intrusion Detection Yisroel Mirsky, Tomer Doitshman, Yuval Elovici and Asaf Shabtai Ben-Gurion University of the Negev yisroel, tomerdoi @post.bgu.ac.il, elovici, shabtaia @bgu.ac.il { } { } Abstract—Neural networks have become an increasingly popu- Over the last decade many machine learning techniques lar solution for network intrusion detection systems (NIDS). Their have been proposed to improve detection performance [2], [3], capability of learning complex patterns and behaviors make them [4]. One popular approach is to use an artificial neural network a suitable solution for differentiating between normal traffic and (ANN) to perform the network traffic inspection. The benefit network attacks. However, a drawback of neural networks is of using an ANN is that ANNs are good at learning complex the amount of resources needed to train them. Many network non-linear concepts in the input data. This gives ANNs a gateways and routers devices, which could potentially host an NIDS, simply do not have the memory or processing power to great advantage in detection performance with respect to other train and sometimes even execute such models. More importantly, machine learning algorithms [5], [2]. the existing neural network solutions are trained in a supervised The prevalent approach to using an ANN as an NIDS is manner. Meaning that an expert must label the network traffic to train it to classify network traffic as being either normal and update the model manually from time to time. or some class of attack [6], [7], [8]. The following shows the In this paper, we present Kitsune: a plug and play NIDS typical approach to using an ANN-based classifier in a point which can learn to detect attacks on the local network, without deployment strategy: supervision, and in an efficient online manner. -

An Introduction to Incremental Learning by Qiang Wu and Dave Snell
Article from Predictive Analytics and Futurism July 2016 Issue 13 An Introduction to Incremental Learning By Qiang Wu and Dave Snell achine learning provides useful tools for predictive an- alytics. The typical machine learning problem can be described as follows: A system produces a specific out- Mput for each given input. The mechanism underlying the system can be described by a function that maps the input to the output. Human beings do not know the mechanism but can observe the inputs and outputs. The goal of a machine learning algorithm is regression, perceptron for classification and incremental princi- to infer the mechanism by a set of observations collected for the pal component analysis. input and output. Mathematically, we use (xi,yi ) to denote the i-th pair of observation of input and output. If the real mech- STOCHASTIC GRADIENT DESCENT anism of the system to produce data is described by a function In linear regression, f*(x) = wTx is a linear function of the input f*, then the true output is supposed to be f*(x ). However, due i vector. The usual choice of the loss function is the squared loss to systematic noise or measurement error, the observed output L(y,wTx) = (y-wTx)2. The gradient of L with respect to the weight y satisfies y = f*(x )+ϵ where ϵ is an unavoidable but hopefully i i i i i vector w is given by small error term. The goal then, is to learn the function f* from the n pairs of observations {(x ,y ),(x ,y ),…,(x ,y )}. -

Computational Science and Engineering
Computational Science and Engineering, PhD College of Engineering Graduate Coordinator: TBA Email: Phone: Department Chair: Marwan Bikdash Email: [email protected] Phone: 336-334-7437 The PhD in Computational Science and Engineering (CSE) is an interdisciplinary graduate program designed for students who seek to use advanced computational methods to solve large problems in diverse fields ranging from the basic sciences (physics, chemistry, mathematics, etc.) to sociology, biology, engineering, and economics. The mission of Computational Science and Engineering is to graduate professionals who (a) have expertise in developing novel computational methodologies and products, and/or (b) have extended their expertise in specific disciplines (in science, technology, engineering, and socioeconomics) with computational tools. The Ph.D. program is designed for students with graduate and undergraduate degrees in a variety of fields including engineering, chemistry, physics, mathematics, computer science, and economics who will be trained to develop problem-solving methodologies and computational tools for solving challenging problems. Research in Computational Science and Engineering includes: computational system theory, big data and computational statistics, high-performance computing and scientific visualization, multi-scale and multi-physics modeling, computational solid, fluid and nonlinear dynamics, computational geometry, fast and scalable algorithms, computational civil engineering, bioinformatics and computational biology, and computational physics. Additional Admission Requirements Master of Science or Engineering degree in Computational Science and Engineering (CSE) or in science, engineering, business, economics, technology or in a field allied to computational science or computational engineering field. GRE scores Program Outcomes: Students will demonstrate critical thinking and ability in conducting research in engineering, science and mathematics through computational modeling and simulations. -

Artificial Intelligence Research For
Charles Xie ([email protected]) is a senior scientist who works at the inter- section between computational science and learning science. Artificial Intelligence research for engineering design By Charles Xie Imagine a high school classroom in 2030. AI is one of the three most promising areas for which Bill Gates Students are challenged to design an said earlier this year he would drop out of college again if he were a young student today. The victory of Google’s AlphaGo against engineering system that meets the needs of a top human Go player in 2016 was a landmark in the history of their community. They work with advanced AI. The game of Go is considered a difficult challenge because computer-aided design (CAD) software that the number of legal positions on a 19×19 grid is estimated to be leverages the power of scientific simulation, 2×10170, far more than the total number of atoms in the observ- mixed reality, and cloud computing. Every able universe combined (1082). While AlphaGo may be only a cool tool needed to complete an engineering type of weak AI that plays Go at present, scientists believe that its development will engender technologies that eventually find design project is seamlessly integrated into applications in other fields. the CAD platform to streamline the learning process. But the most striking capability of Performance modeling the software is its ability to act like a mentor (e.g., simulation-based analysis) who has all the knowledge about the design project to answer questions, learns from all the successful or unsuccessful solutions ever Evaluator attempted by human designers or computer agents, adapts to the needs of each student based on experience interacting with all sorts of designers, inspires students to explore creative ideas, and, most importantly, remains User Ideator responsive all the time without ever running out of steam. -

An Evaluation of Tensorflow As a Programming Framework for HPC Applications
DEGREE PROJECT IN COMPUTER SCIENCE AND ENGINEERING, SECOND CYCLE, 30 CREDITS STOCKHOLM, SWEDEN 2018 An Evaluation of TensorFlow as a Programming Framework for HPC Applications WEI DER CHIEN KTH ROYAL INSTITUTE OF TECHNOLOGY SCHOOL OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE An Evaluation of TensorFlow as a Programming Framework for HPC Applications WEI DER CHIEN Master in Computer Science Date: August 28, 2018 Supervisor: Stefano Markidis Examiner: Erwin Laure Swedish title: En undersökning av TensorFlow som ett utvecklingsramverk för högpresterande datorsystem School of Electrical Engineering and Computer Science iii Abstract In recent years, deep-learning, a branch of machine learning gained increasing popularity due to their extensive applications and perfor- mance. At the core of these application is dense matrix-matrix multipli- cation. Graphics Processing Units (GPUs) are commonly used in the training process due to their massively parallel computation capabili- ties. In addition, specialized low-precision accelerators have emerged to specifically address Tensor operations. Software frameworks, such as TensorFlow have also emerged to increase the expressiveness of neural network model development. In TensorFlow computation problems are expressed as Computation Graphs where nodes of a graph denote operation and edges denote data movement between operations. With increasing number of heterogeneous accelerators which might co-exist on the same cluster system, it became increasingly difficult for users to program efficient and scalable applications. TensorFlow provides a high level of abstraction and it is possible to place operations of a computation graph on a device easily through a high level API. In this work, the usability of TensorFlow as a programming framework for HPC application is reviewed. -

A Brief Introduction to Mathematical Optimization in Julia (Part 1) What Is Julia? and Why Should I Care?
A Brief Introduction to Mathematical Optimization in Julia (Part 1) What is Julia? And why should I care? Carleton Coffrin Advanced Network Science Initiative https://lanl-ansi.github.io/ Managed by Triad National Security, LLC for the U.S. Department of Energy’s NNSA LA-UR-21-20278 Warning: This is not a technical talk! 9/25/2019 Julia_prog_language.svg What is Julia? • A “new” programming language developed at MIT • nearly 10 years old (appeared around 2012) • Julia is a high-level, high-performance, dynamic programming language • free and open source • The Creator’s Motivation • build the next-generation of programming language for numerical analysis and computational science • Solve the “two-language problem” (you havefile:///Users/carleton/Downloads/Julia_prog_language.svg to choose between 1/1 performance and implementation simplicity) Who is using Julia? Julia is much more than an academic curiosity! See https://juliacomputing.com/ Why Julia? Application9/25/2019 Julia_prog_language.svg Needs Data Scince Numerical Scripting Computing Automation 9/25/2019 Thin-Border-Logo-Text Julia Data Differential Equations file:///Users/carleton/Downloads/Julia_prog_language.svg 1/1 Deep Learning Mathematical Optimization High Performance https://camo.githubusercontent.com/31d60f762b44d0c3ea47cc16b785e042104a6e03/68747470733a2f2f7777772e6a756c69616f70742e6f72672f696d616765732f6a7… 1/1 -

Adversarial Examples: Attacks and Defenses for Deep Learning
1 Adversarial Examples: Attacks and Defenses for Deep Learning Xiaoyong Yuan, Pan He, Qile Zhu, Xiaolin Li∗ National Science Foundation Center for Big Learning, University of Florida {chbrian, pan.he, valder}@ufl.edu, [email protected]fl.edu Abstract—With rapid progress and significant successes in a based malware detection and anomaly detection solutions are wide spectrum of applications, deep learning is being applied built upon deep learning to find semantic features [14]–[17]. in many safety-critical environments. However, deep neural net- Despite great successes in numerous applications, many of works have been recently found vulnerable to well-designed input samples, called adversarial examples. Adversarial examples are deep learning empowered applications are life crucial, raising imperceptible to human but can easily fool deep neural networks great concerns in the field of safety and security. “With great in the testing/deploying stage. The vulnerability to adversarial power comes great responsibility” [18]. Recent studies find examples becomes one of the major risks for applying deep neural that deep learning is vulnerable against well-designed input networks in safety-critical environments. Therefore, attacks and samples. These samples can easily fool a well-performed defenses on adversarial examples draw great attention. In this paper, we review recent findings on adversarial examples for deep learning model with little perturbations imperceptible to deep neural networks, summarize the methods for generating humans. adversarial examples, and propose a taxonomy of these methods. Szegedy et al. first generated small perturbations on the im- Under the taxonomy, applications for adversarial examples are ages for the image classification problem and fooled state-of- investigated. -

From Computational Science to Science Discovery
FromComputationalSciencetoScienceDiscovery:The NextComputingLandscape GiladShainer,BrianSparks,ScotSchultz,EricLantz,WilliamLiu,TongLiu,GoldiMisra HPCAdvisoryCouncil {Gilad,Brian,Scot,Eric,William,Tong,[email protected]} Computationalscienceisthefieldofstudyconcernedwithconstructingmathematicalmodelsand numericaltechniquesthatrepresentscientific,socialscientificorengineeringproblemsandemploying thesemodelsoncomputers,orclustersofcomputerstoanalyze,exploreorsolvethesemodels. Numericalsimulationenablesthestudyofcomplexphenomenathatwouldbetooexpensiveor dangeroustostudybydirectexperimentation.Thequestforeverhigherlevelsofdetailandrealismin suchsimulationsrequiresenormouscomputationalcapacity,andhasprovidedtheimpetusfor breakthroughsincomputeralgorithmsandarchitectures.Duetotheseadvances,computational scientistsandengineerscannowsolvelargeͲscaleproblemsthatwereoncethoughtintractableby creatingtherelatedmodelsandsimulatethemviahighͲperformancecomputeclustersor supercomputers.Simulationisbeingusedasanintegralpartofthemanufacturing,designanddecisionͲ makingprocesses,andasafundamentaltoolforscientificresearch.ProblemswherehighͲperformance simulationplayapivotalroleincludeforexampleweatherandclimateprediction,nuclearandenergy research,simulationanddesignofvehiclesandaircrafts,electronicdesignautomation,astrophysics, quantummechanics,biology,computationalchemistryandmore. Computationalscienceiscommonlyconsideredthethirdmodeofscience,wherethepreviousmodesor paradigmswereexperimentation/observationandtheory.Inthepast,sciencewasperformedby -

Deep Learning and Neural Networks Module 4
Deep Learning and Neural Networks Module 4 Table of Contents Learning Outcomes ......................................................................................................................... 5 Review of AI Concepts ................................................................................................................... 6 Artificial Intelligence ............................................................................................................................ 6 Supervised and Unsupervised Learning ................................................................................................ 6 Artificial Neural Networks .................................................................................................................... 8 The Human Brain and the Neural Network ........................................................................................... 9 Machine Learning Vs. Neural Network ............................................................................................... 11 Machine Learning vs. Neural Network Comparison Table (Educba, 2019) .............................................. 12 Conclusion – Machine Learning vs. Neural Network ........................................................................... 13 Real-time Speech Translation ............................................................................................................. 14 Uses of a Translator App ................................................................................................................... -

Re-Purposing Commercial Entertainment Software for Military Use
Calhoun: The NPS Institutional Archive Theses and Dissertations Thesis Collection 2000-09 Re-purposing commercial entertainment software for military use DeBrine, Jeffrey D. Monterey, California. Naval Postgraduate School http://hdl.handle.net/10945/26726 HOOL NAV CA 9394o- .01 NAVAL POSTGRADUATE SCHOOL Monterey, California THESIS RE-PURPOSING COMMERCIAL ENTERTAINMENT SOFTWARE FOR MILITARY USE By Jeffrey D. DeBrine Donald E. Morrow September 2000 Thesis Advisor: Michael Capps Co-Advisor: Michael Zyda Approved for public release; distribution is unlimited REPORT DOCUMENTATION PAGE Form Approved OMB No. 0704-0188 Public reporting burden for this collection of information is estimated to average 1 hour per response, including the time for reviewing instruction, searching existing data sources, gathering and maintaining the data needed, and completing and reviewing the collection of information. Send comments regarding this burden estimate or any other aspect of this collection of information, including suggestions for reducing this burden, to Washington headquarters Services, Directorate for Information Operations and Reports, 1215 Jefferson Davis Highway, Suite 1204, Arlington, VA 22202-4302, and to the Office of Management and Budget, Paperwork Reduction Project (0704-0188) Washington DC 20503. 1 . AGENCY USE ONLY (Leave blank) 2. REPORT DATE REPORT TYPE AND DATES COVERED September 2000 Master's Thesis 4. TITLE AND SUBTITLE 5. FUNDING NUMBERS Re-Purposing Commercial Entertainment Software for Military Use 6. AUTHOR(S) MIPROEMANPGS00 DeBrine, Jeffrey D. and Morrow, Donald E. 8. PERFORMING 7. PERFORMING ORGANIZATION NAME(S) AND ADDRESS(ES) ORGANIZATION REPORT Naval Postgraduate School NUMBER Monterey, CA 93943-5000 9. SPONSORING / MONITORING AGENCY NAME(S) AND ADDRESS(ES) 10. SPONSORING/ Office of Economic & Manpower Analysis MONITORING AGENCY REPORT 607 Cullum Rd, Floor IB, Rm B109, West Point, NY 10996-1798 NUMBER 11.